This will allow you to collect domain computer event logs real-time (they really are real-time).
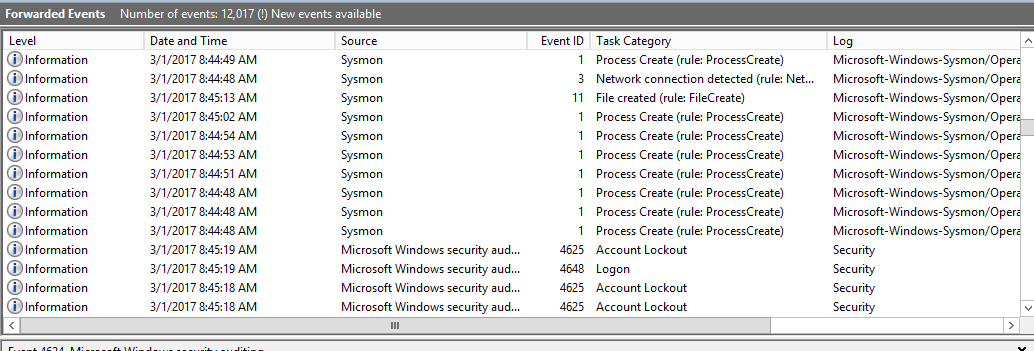
Here’s an example of how they would display.
Here’s an example of how they would display.
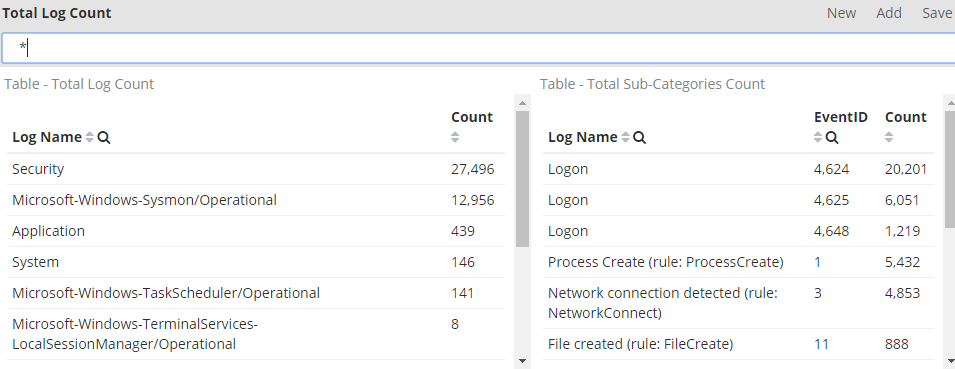
Once you are done with this series, you may want to send your WEF logs to Elasticsearch and visualize them on Kibana as that is our end goal.
Here’s some of your future dashboards
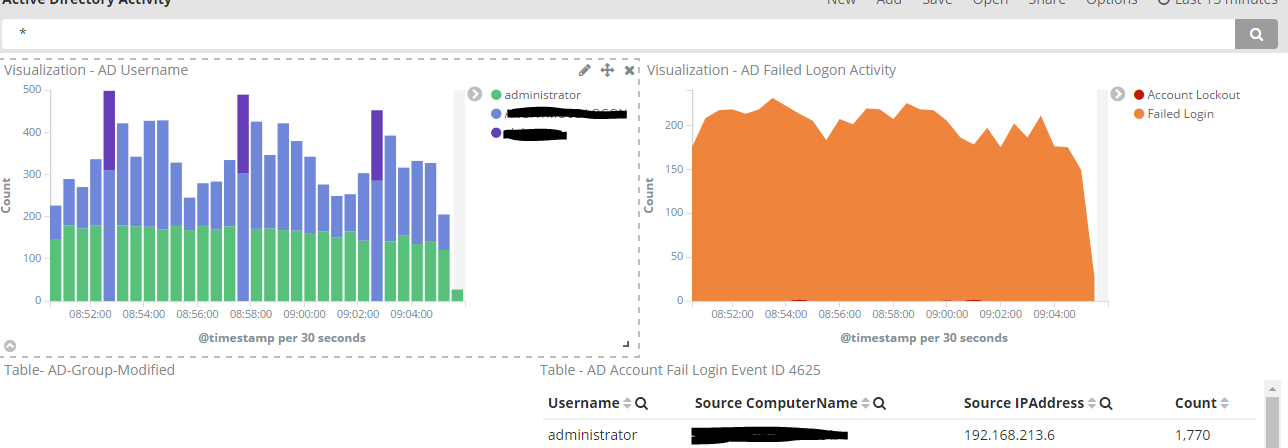
Anyways, let’s get started.
Prerequisites:
- Windows Server for log collection in a domain environment.
- Create a computer group in your domain (my example will be WEF Computers)
Step 1: Setting up WEF
1. Log in to Windows server in this case (WindowsLogCollector)
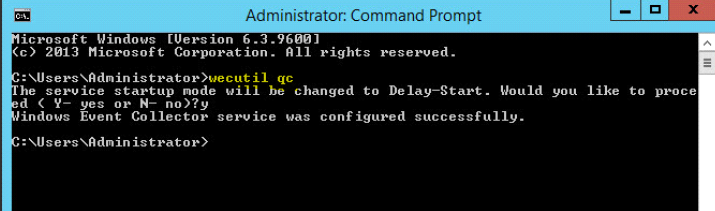
2. Launch command prompt nad type: wecutil qc
Hit Y to procceed.
Hit Y to procceed.
(note: Wecutil.exe is a Windows Event Collector utility that enables an administrator to create and manage subscriptions to events forwarded from remote event sources that support the WS-Management protocol.)
Step 2: Setting up Event Subcriptions
1. Browse to Event Viewer
2. Right click Subscriptions and create subscription
2. Right click Subscriptions and create subscription
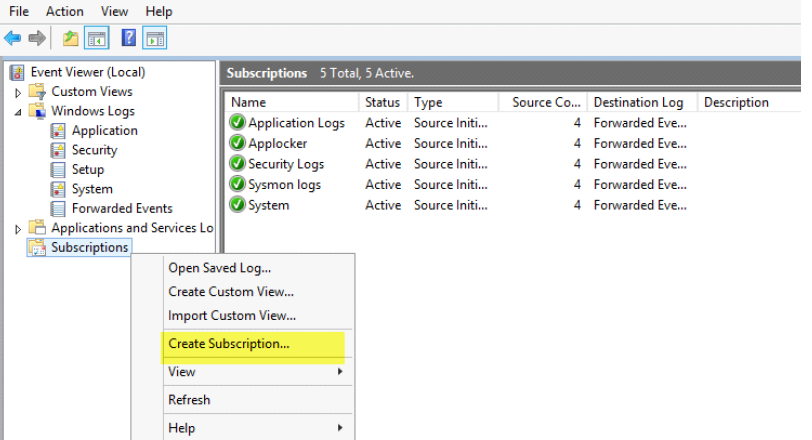
3. Provide a meaningful subscription name (e.g Application, Security, System)
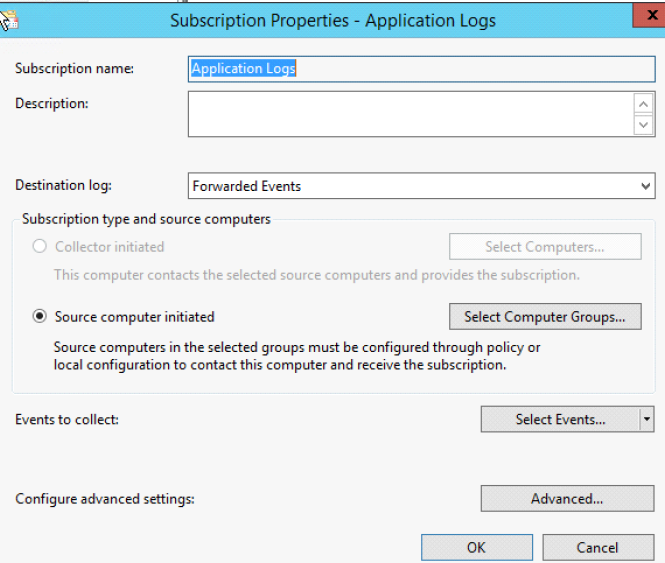
4. Click on Select Computer Groups and add the computer group you’d like to see. In this example I have a computer group called WEF Computers. Now we Add Domain Computers and click OK. (Alternatively, you can add individual systems here as well)

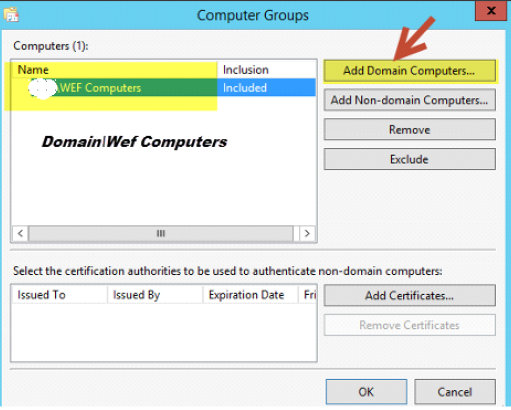
Click “OK” once done.
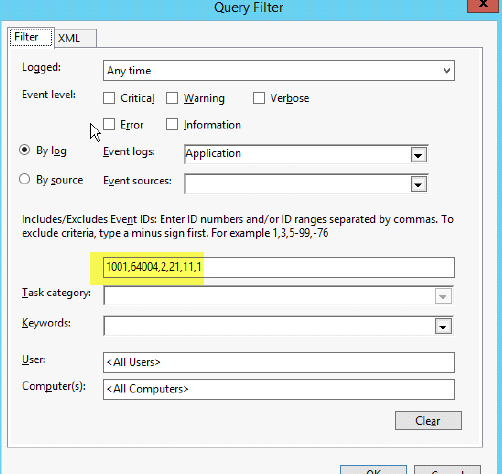
5. Next Select Select Events and choose the type of logs that you want. (note, if you are unsure what logs to get, just check the event level boxes so you may grab all logs). We limited this to a few selected ones that we’re interested in.

6. Lastly, select Advanced and fill in the option Minimize Latency

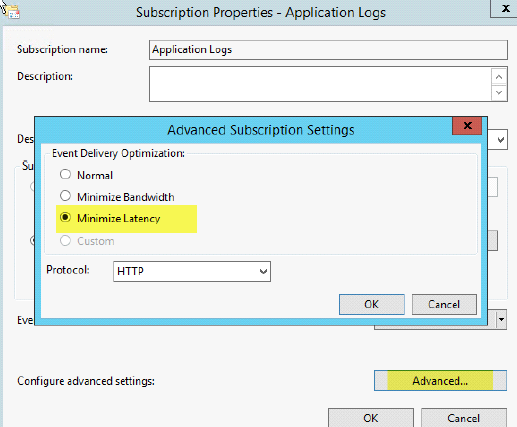
Hit OK
You have now created your first Windows Event Forwarder Subscription. Repeat the steps for other logs such as System, Sysmon (See part 2 of this series), etc.
Not sure what Logs to monitor?
Below is a list of Event IDs along with a description. I have a longer list saved; however, these are the ones I believe should be monitored.
Security Logs:
| EventID | Description | Source |
| 4756 | A member was added to a security-enabled universal group | Security |
| 4740 | A User account was Locked out | Security |
| 4735 | A security-enabled local group was changed | Security |
| 4732 | A member was added to a security-enabled local group | Security |
| 4728 | A member was added to a security-enabled global group | Security |
| 4724 | An attempt was made to reset an accounts password | Security |
| 4648 | A logon was attempted using explicit credentials | Security |
| 4625 | An account failed to log on | Security |
| 1102 | The Audit Log was cleared | System |
| 4624 | An accout was successfully logged on | Security |
| 4634 | An account was logged off | Security |
| 5038 | Detected an invalid image hash of a file | Security |
| 6281 | Detected an invalid page hash of an image file | Security |
Application Logs
| EventID | Description | Source | Log Name |
| 1000 | Application Error | Application | |
| 1002 | Application Hang- Crash | Application | |
| 1001 | Application Error – Fault Bucket | Application | |
| 1 | EMET | ||
| 2 | EMET |
System:
| EventID | Description | Source |
| 104 | Event Log Cleared | System |
| 1102 | The Audit Log was cleared | System |
| 4719 | System Audit Policy was changed | System |
| 6005 | Event log Service Stopped | System |
| 7022-7026,7031,7032,7034 | Windows Services Fails or crashes | System |
| 7045 | A service was installed in the system | System |
| 4697 | A service was installed in the system | System |
| 7022 | EVENT_SERVICE_START_HUNG | System |
| 7023 | EVENT_SERVICE_EXIT_FAILED | System |
| 104 | Event log was cleared | System |
| 6 | New Kernel Filter Driver | System |
Firewall
| EventID | Description | Source | Log Name |
| 2005 | A Rule has been modified in the WindowS firewall Exception List | Firewall | Microsoft-Windows-Windows Firewall With Advanced Security/Firewall |
| 2004 | Firewall Rule Add | ||
| 2006, 2033 | Firewall Rules Deleted | ||
| 2009 |
Terminal Services
| EventID | Description | Source | Log Name |
| 23 | Session Logoff Scceeded | TerminalServices-LocalSessionManager | Microsoft-Windows-TerminalServices-LocalSessionManager/Operational |
| 24 | Session has been disconnected | TerminalServices-LocalSessionManager | Microsoft-Windows-TerminalServices-LocalSessionManager/Operational |
| 25 | Session Reconnection Succeded | TerminalServices-LocalSessionManager | |
| 1102 | Client has initiated a multi-transport connection | TerminalServices-ClientActiveXCor | Microsoft-Windows-TerminalServices-RDPClient/Operational |
========================================================================
We will be setting up Sysmon in our WEF server. As you saw in the previous article, there is no option for Sysmon subscription under event viewer. Let’s resolve that.
Step 1: Setup Sysmon
Download Sysmon from here: https://technet.microsoft.com/en-us/sysinternals/sysmon
Download Sysmon from here: https://technet.microsoft.com/en-us/sysinternals/sysmon
1. Extract to a local destination
2.Launch a command prompt with elevated privileges(right click-run as Administrator)
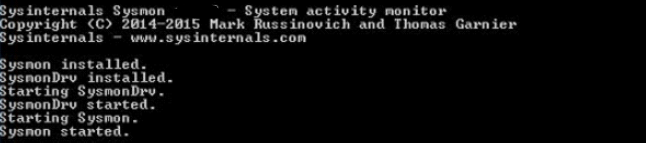
3.Run the following command: Sysmon.exe -I -h sha256 -n /accepteula
4.You should then see a message similar to the screenshot below, and eventually see the service Sysmon getting started.
2.Launch a command prompt with elevated privileges(right click-run as Administrator)
3.Run the following command: Sysmon.exe -I -h sha256 -n /accepteula
4.You should then see a message similar to the screenshot below, and eventually see the service Sysmon getting started.
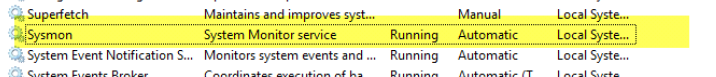
5. Verify that sysmon is running by going to windows services. 
6. Reboot your system.
7. Now go back and create a new subscription for Sysmon
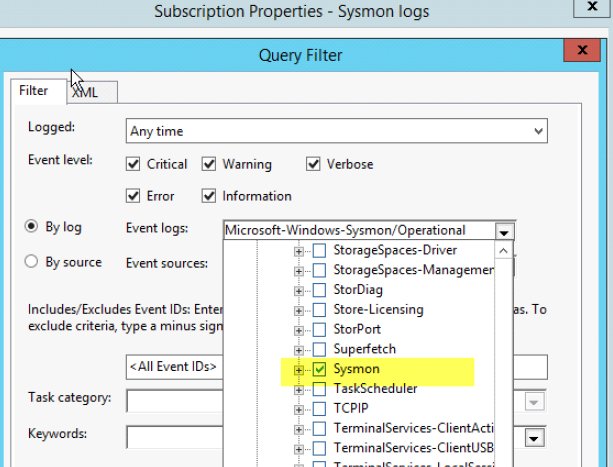
Done!
Now that you have setup a Windows Event Forwarder collector + Sysmon subscriptions, you are now ready to collect these logs from your endpoint.
We will now create a group policy and deploy it to our systems.
Prerequisites:
- Create computer OU for GPO deployment (WEF Deployment)
Creating GPO
Step 1: Create WinRM Service and set it to start automatically
Launch your group policy utility and perform the following:
- Right click your computer OU and
- Create GPO in this domain, and link it here
- Provide a name (WEF Deployment) , click OK
- Right click your newly created GPO WEF Deployment and select Edit
- Navigate to Computer Configuration > Preferences > Control Panel Settings > “New > Service”
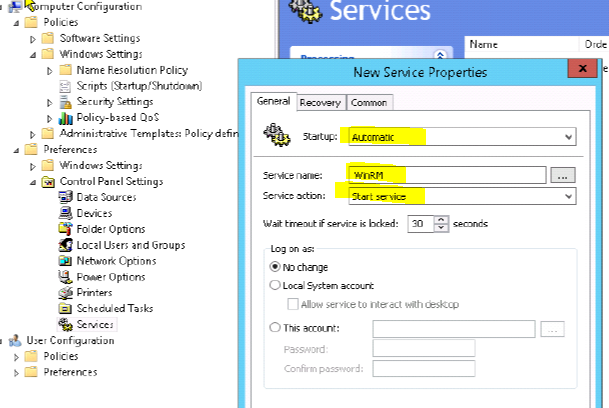
Startup: AutomaticService
Name: WinRMService
Action: Start service
Click Apply
Step 2: Provide Event Log Reader Access
In this step we will add the Network Service & Event Forwarder Server (WindowsLogCollector) to the Event Log Readers and Groups. This will give our WEF server (WindowsLogCollector) access to your domain endpoint event logs.
- Right click your WEF Deployment GPO and select Edit
- Computer Configuration > Preferences > Control Panel Settings > right click > “New Group”
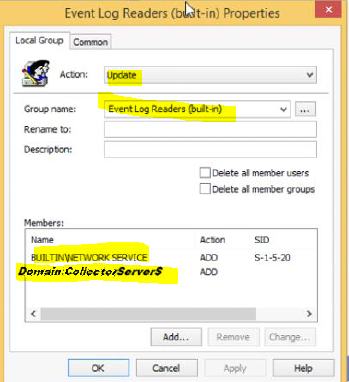
Action: Update
Group Name: Event Log Readers
Members: NETWORK SERVICE
Domain\WindowsLogCollector$
Apply > OK
Step 3: Adding WEF Server Subscription addressThis will allow our endpoints to enroll to our WindowsLogCollector subscriptions.
- Right click your WEF Deployment GPO and select Edit
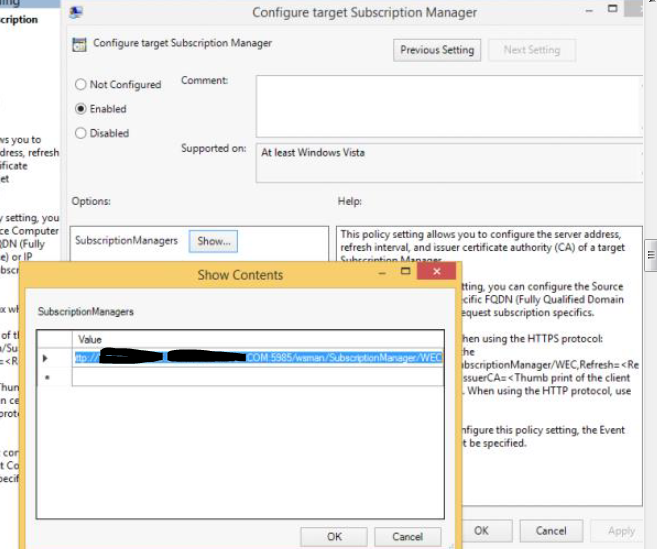
- Computer Configuration > Policies > Administrative Templates > Windows Components > Event Forwarding > Configure target Subscription Manager >
- Set to EnableShow: Server=http://WindowsLogCollector.domain.COM:5985/wsman/SubscriptionManager/WEC
Click OK

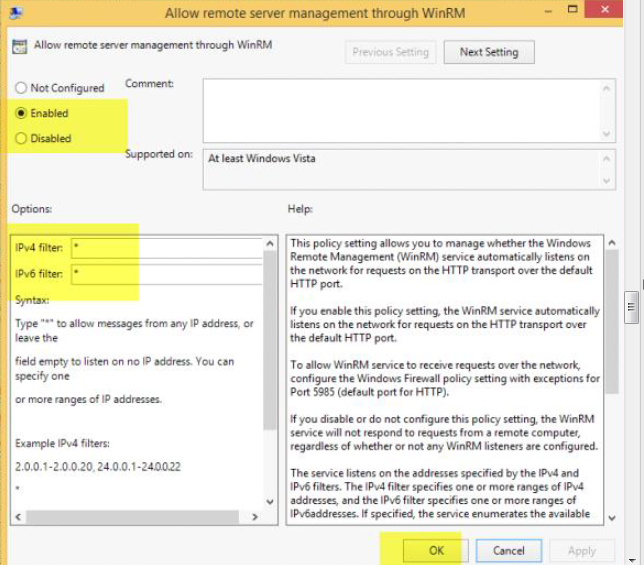
Step 4: Allow Remote server Management through WinRM
- Right click your WEF Deployment GPO and select Edit
- Computer Configuration > Policies > Administrative Templates > Windows Components > Windows Remote Management (WinRM) > WinRMService > Allow Remote Server Management through WinRM
Set: EnableiPv4 Filter: * (or you may enter just the IP address of your WindowsLogCollector)
IpV6 Filter: * (you may uncheck this)
OK
We are now done!
Go back to your WindowsLogCollector server and browse to the Event Viewer, you should see the endpoints start to register and logs under Fowarded Events.
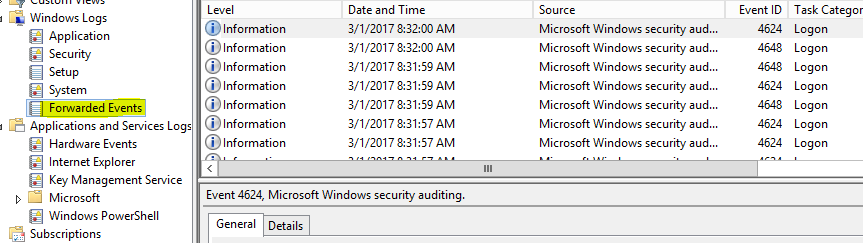
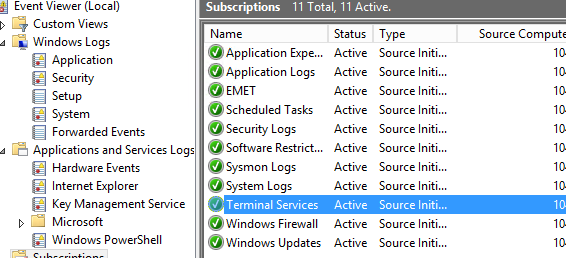
(Note: This might take up to 90 min depending on how often our GPO refreshes. You may want to run gpupdate /force on your endpoints to refresh group policy and receive these changes immediately. Additionally, it may take up to 15 minutes for your endpoints to receive a subscription updates whenever you add or remove an event ID when creating Subscriptions. You may restart the Windows Remote Management (WS-Management) (WinRM) service to trigger the request to our WEF server and receive the update instantly).
Important Note: If you are collecting Security logs, once your endpoint gets the subscription settings, you will need to restart that particular endpoint so the permissions apply and allow you to collect security logs. Otherwise you will be frustrated about not receiving Security Event logs.
Additionally, since you want to collect all endpoint logs, it would be useful to deploy Sysmon to all of your endpoints as well, you may follow this guide on how to accomplish this.
from: https://www.syspanda.com/index.php/2017/03/01/setting-up-windows-event-forwarder-server-wef-domain-gpo-deployment-part-33/

No comments:
Post a Comment