https://mp.weixin.qq.com/s/CzrQoLdpVUHrXGTMrkWHPQ
序:
知彼知己,百战不殆;在作战过程中,如果对敌我双方的情况都能了解透彻,就能够打胜仗。
---- 《孙子·谋攻》
纵观网空安全领域近十年的发展,不难发现,网空安全领域的很多重要的理念和理论都深受军事领域的思想和理论的影响。尤其是威胁情报此类带有浓厚的军事色彩的理论,因此,笔者建议,读者在理解威胁情报的时候,应从军事领域的情报角度入手,以便从更高的视角深入理解威胁情报,不宜将思维局限于网空安全领域。
目录:
威胁情报的定义
威胁情报的核心概念:“三问题规则”和四个主要属性
威胁情报的分类:战术情报、运营情报、战略情报
威胁情报的相关标准:STIX™和TAXII™
威胁情报的应用:整合事件响应工作流
威胁情报的价值呈现
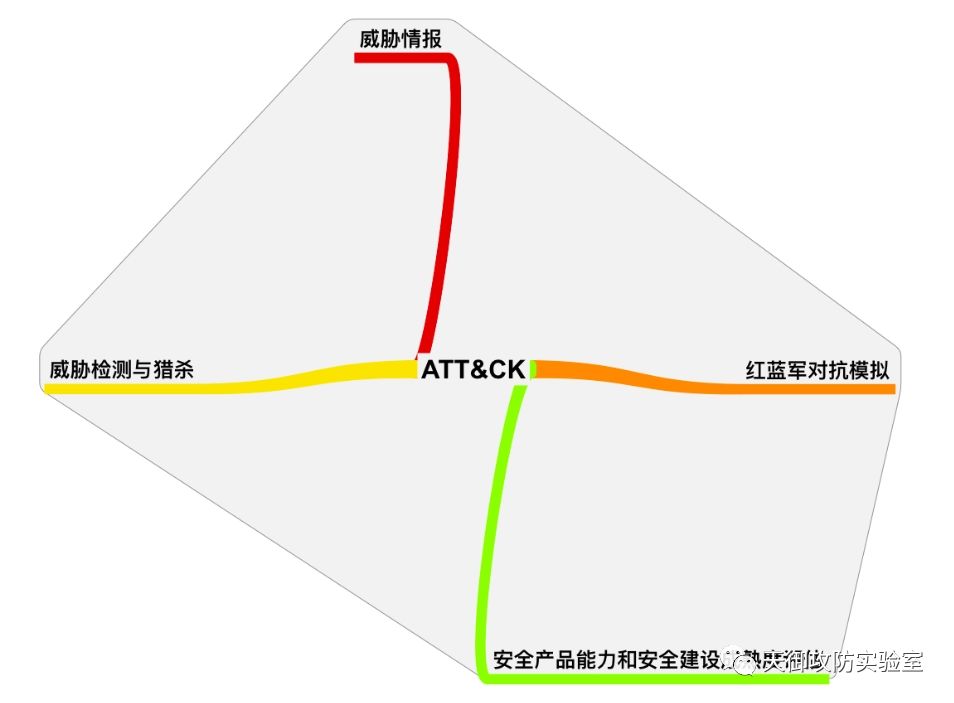
威胁情报和ATT&CK™模型
参考资料!
致谢!
1.威胁情报的定义
许多机构曾提出过威胁情报的定义,这里我们从攻防的角度给出一个定义,同时给出Gartner关于威胁情报的定义可作为参考或对比。
威胁情报是对攻击者及其恶意活动的可运营的知识(actionable knowledge)和洞见(insight),使防御者及其组织能够通过更好的安全决策来降低安全风险。
知识包括上下文、机制、指标、含义和可执行的建议。这些知识使防御者及其组织能够改进他们的安全决策。当安全团队利用“洞见(insight)”来改善他们的整个网络安全态势时,威胁情报可以降低安全风险。
Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject's response to that menace or hazard. ---- Gartner
威胁情报是某种基于证据的知识,包括上下文、机制、指标、含义和可执行的建议,这些知识与资产所面临已有的或酝酿中的威胁或危害相关,可用于对这些威胁或危害进行响应的相关决策提供信息支持。----- Gartner
上下文,威胁元素相关的多维度属性的标定和描述,不同层次的威胁情报有其对应的不同属性集,除此之外上下文可能还会包括时间与环境相关的信息。
IP上下文属性
所在ASN域、地理位置、是否代理、近期是否存在相关恶意活动、网络出口类型、历史和当前绑定过的域名、开放的端口和服务
文件样本上下文属性
文件是否恶意、恶意类型、恶意代码家族、是否定向攻击中使用、相关的网络行为
APT组织上下文属性
组织名字及别名、来源国家地区、攻击目的、目标行业、攻击方法手段、技术能力
整合威胁情报到企业安全建设计划中,可以有效减少dwell time(攻击者首次入侵到被发现,在受害者网络中的停留(或潜伏)时间。)和MTTC(检测到事件后,企业采取遏制措施平均所需的时间。)。
威胁情报详细说明了对手如何攻陷和破坏系统,以便防御者可以更好地准备在事前、事中和事后进行预防、检测和响应攻击者的行为。
威胁情报通过使用多种数据(5W1H)来生成关于对手的知识,从而实现这一目标,例如:
- 对手是谁(Who),包括威胁行为体,赞助商和雇主
- 对手使用什么(What),包括他们的能力和基础设施
- 对手的行动时(When),确定行动的时间表和规律
- 对手的目的(Why),包括他们的动机和意图
- 对手的目标行业和地理区域(Where),详细说明行业,垂直行业和地理区域
- 对手如何运作(How),专注于他们的行为和规律
2.威胁情报的核心概念:“三问题规则”和四个主要属性
2.1)威胁情报的“三问题规则”
所有威胁情报都应解决三个问题,使客户能够快速确定其组织的相关性和影响,然后在必要时立即采取行动。
- 威胁(Threat)- 威胁是什么?who, what where, when why 和how。
- 影响(Impact)- 对组织的影响是什么?
- 行动(Action,可执行的建议)- 哪些行动可以缓解近期和中期的威胁?
威胁情报通过定义上下文来解决这些问题。谁应该关注威胁和原因,以及通过定义要采取的行动 – 如何保护和防御它。在没有上下文的情况下,威胁情报缺乏支持决策的必要描述性元素,例如检测优先级或威胁与环境的相关性。如果没有采取行动,威胁情报对于组织而言往往毫无用处。
威胁情报上下文
威胁情报上下文提供围绕任何威胁的必要相关性。
威胁情报上下文通常包括:
- 每个钻石模型(Diamond Model)特征的描述
- 整个杀伤链(Kill Chain)中对手行为的描述
- 技术说明,包括网络活动,恶意软件分析以及主机和日志活动
- 对熟悉的操作环境进行影响评估,方案和风险分析
- 进一步研究的重要参考资料
威胁情报上下文示例:
影响:高
行业:电力传输
2018年12月10日至30日期间,几家涉及电力传输的公用事业公司受到鱼叉式网络钓鱼电子邮件攻击。这些电子邮件包含一个恶意Word文档,在未打安全补丁的电脑上成功利用漏洞MS08-067,然后开始通过SMBv1在网络中传播类似蠕虫的活动,进行横向移动。该蠕虫主动寻找历史学家的应用以及涉及电力传输的运营网络的其他证据。
一旦蠕虫发现了运营网络的证据,蠕虫就会通过HTTPS向IP X.X.X.X联系命令和控制服务器。然后,攻击者将使用蠕虫的远程访问功能访问网络,并使用本地PowerShell资源开始进一步的内部侦察。
该威胁主要针对电力传输行业,因此可能与该行业以外的组织无关。但是,不排除攻击者会攻击其他行业,因此我们建议网络维护者或运营商根据我们上面提供的技术细节,进行自检,以防止将来对其网络的此类攻击。
参考资料:xxx
威胁情报行动(可执行的建议)
威胁情报行动提供针对威胁行为和影响而定制的技术和方案建议。行动的范围从检测和猎杀的技术细节到对公司管理层有用的最具战略性的洞见。
威胁情报行动通常包括:
- 检测指导,如失陷指标(IOCs)或签名(signatures),以支持识别入侵行为
- 保护组织免受潜在威胁的指导方案
- 详细的威胁行为,以寻找类似的行为
- 支持有效检测的数据收集建议
- 威胁范围和影响细节支持基于风险的战略决策
威胁情报行动示例:
在2017年7月10日至8月30日期间检测并防止与IP地址X.X.X.X相关的任何入站或出站网络活动,因为它被用作恶意活动的命令和控制。
安装MS08-067补丁,以防止被攻击者利用。
屏蔽IT和运营网络之间的SMBv1通信,以防止蠕虫的潜在传播。如果SMBv1是业务运营所必需的,我们建议运营网络限制除必要位置之外的所有SMBv1活动/流量。
进入受害者网络后,攻击者会利用Windows PowerShell进行进一步的渗透-我们建议监视所有PowerShell活动以查找与所述活动相关的行为,并在不需要的所有主机上禁用PowerShell。
由于这种威胁对运营的影响很大(包括电力传输损失),建议与该活动有关的每个组织优先考虑此威胁。
2.2)威胁情报的四个主要属性
好的威胁情报必须具备四个属性:完整性(completeness),准确性(accuracy),相关性(relevance)和及时性(timeliness)。
- 完整性(completeness):威胁情报必须提供足够的细节以实现正确的响应,如主机取证,恶意软件分析,漏洞分析,网络流量分析和日志分析。
- 准确性(accuracy):这对应着我们一般说的误报率指标。
- 相关性(relevance):强调和具体用户的地域性、行业性相关,即需要针对此用户的环境,能发现可能遭遇的重要威胁。
- 及时性或时效性(timeliness):情报的及时性是由多个因素构成的,从数据收集,云端处理到情报分发(即收集、处理和分发的及时性)。另外,情报不仅需要标记生成时间而且需要标注持续时间。情报的域名拥有者、IP使用者和其上的业务,随着时间的推移,可能产生变化,黑IP会变成白IP。
3.威胁情报的分类:战术情报、运营情报、战略情报
按照目标受众及其影响范围和作用我们将威胁情报分为三类:战术(tactical),运营(operational)和战略(strategic)。
情报类型 | 使用者 | 描述 |
战术情报 | SOC操作、安全运维团队 | 为网络级别行动和补救提供信息的技术指标和行为 |
运营情报 | 事件事件响应、威胁分析检测团队、安全负责人 | 关于对手行为的情报:整体补救,威胁搜寻,行为检测,购买决策和数据收集。 |
战略情报 | CISO、CSO | 描绘当前对于特定组织的威胁类型和对手现状,以辅助决策 |
战术情报:以自动化检测分析为主
运营情报:以安全响应分析为目的
战略情报:以及指导整体安全投资策略
战术级情报
战术情报,标记攻击者所使用工具相关的特征值及网络基础设施信息(文件HASH、IP、域名、程序运行路径、注册表项等),其作用主要是发现威胁事件以及对报警确认或优先级排序。常见的失陷检测情报(C2情报)、IP地址情报就属于这个范畴,它们都是可机读的情报,可以直接被设备使用,自动化的完成上述的安全工作。
失陷检测情报,即攻击者控制被害主机所使用的远程命令与控制服务器情报。情报的IOC往往是域名、IP、URL形式,这种IOC可以推送到不同的安全设备中,如NGFW、IPS、SIEM等,进行检测发现甚至实时阻截。这类情报基本上都会提供危害等级、攻击团伙、恶意家族等更丰富的上下文信息,来帮助确定事件优先级并指导后续安全响应活动。使用这类情报是及时发现已经渗透到组织APT团伙、木马蠕虫的最简单、及时、有效的方式。
IP情报是有关访问互联网服务器的IP主机相关属性的信息集合,许多属性是可以帮助服务器防护场景进行攻击防御或者报警确认、优先级排序工作的。譬如:利用持续在互联网上进行扫描的主机IP信息,可以防止企业资产信息被黑客掌握(很多时候黑客对那些主机开放了SMB端口、哪些可能有Struts2漏洞比企业的网管掌握的更清楚);利用在互联网进行自动化攻击的IP信息可以用来进行Web攻击的优先级排序;利用IDC主机或终端用户主机IP信息可以用来进行攻击确认、可疑行为检测或垃圾邮件拦截;而网关IP、代理IP等也都各自有不同的作用,相关场景很多,就不一一列举了。
运营级情报
运营级情报,描述攻击者的战术、技术及过程,即所谓的TTP(Tactics、Technique、Procedure),这是相对战术情报抽象程度更高的威胁信息,是给威胁分析师或者说安全事件响应人员使用的,目的是对已知的重要安全事件做分析(报警确认、攻击影响范围、攻击链以及攻击目的、技战术方法等)或者利用已知的攻击者技战术手法主动的查找攻击相关线索。第一类活动属于事件响应活动的一部分,第二类活动更是有一个高大上的名字“威胁猎杀”。
事件响应活动中的安全分析需要本地的日志、流量和终端信息,需要企业有关的资产情报信息,也需要运营级威胁情报。这种情况下情报的具体形式往往是威胁情报平台这样为分析师使用的应用工具。有一个和攻击事件相关的域名或IP,利用这个平台就有可能找到和攻击者相关更多攻击事件及详情,能够对攻击目的、技战术手法有更多的认识;通过一个样本,我们能够看到更多的相关样本,也可以对样本的类型、流行程度、样本在主机上的行为特征有更多的了解;同样的利用这个平台可以持续的跟踪相关的攻击者使用的网络基础设施变化;发现相关资产是否已经被攻击者所利用,等等。
威胁猎杀是一个基于已知技战术手法(TTP:战术、技术、过程)发现未知威胁事件,同时获得进一步黑客技战术相关信息的过程。威胁猎杀的过程需要特定的内部日志、流量或终端数据和相应分析工具,还需要掌握有较丰富对手技战术手法的安全分析师。这类情报往往通过基于安全事件的分析报告,或者特定的技战术手法数据库得到,国际上在这方面已经有较多的进展,包括了各类开源或限定范围的来源可以提供这样的信息,而国内相对较少,并且一些安全事件报告因为这样那样的问题,并不能公开发表最宝贵的TTP层面分析内容。
战略级情报
战略层面的威胁情报,描绘当前对于特定组织的威胁类型和对手现状,指导安全投资的大方向,是给组织的安全管理者使用的,比如CSO、CISO。一个组织在安全上的投入有多少,应该投入到那些方向,往往是需要在最高层达成一致的。但面临一个问题,如何让对具体攻防技术并不清楚的业务管理者得到足够的信息,来确定相关的安全投资等策略?这时候如果CSO手中有战略层面的情报,就会成为有力的武器。它包括了什么样的组织会进行攻击,攻击可能造成的危害有哪些,攻击者的战术能力和掌控的资源情况等,当然也会包括具体的攻击实例。有了这样的信息,安全投入上的决策就不再是盲目的、而是更符合组织的业务状况及面临的真实威胁。
4.威胁情报的相关标准:STIX™和TAXII™
4.1)STIX™(结构化威胁信息表达)
结构化威胁信息表达(STIX™)是一种用于交换网络威胁情报(CTI)的语言和序列化(JSON)格式。网络威胁情报是描述有关对手及其行为的信息。例如,知道某些对手通过使用定制的钓鱼电子邮件来定向攻击金融机构,对于防御攻击非常有用。STIX以机器可读形式捕获这种类型的情报,以便可以在组织和工具之间共享。
4.2)TAXII™(情报信息的可信自动化交换)
情报信息的可信自动化交换(TAXII)是用来基于HTTPS交换威胁情报信息的一个应用层协议。TAXII是为支持使用STIX描述的威胁情报交换而专门设计的,但是也可以用来共享其他格式的数据。需要注意的是,STIX和TAXII是两个相互独立的标准,也就是说,STIX的结构和序列化不依赖于任何特定的传输机制,而TAXII也可用于传输非STIX数据。
使用TAXII规范,不同的组织机构之间可以通过定义与通用共享模型相对应的API来共享威胁情报。
实例:
https://oasis-open.github.io/cti-documentation/examples/
STIX 2.0 示例剖析
https://mp.weixin.qq.com/s/B88yOz9UWRm5WhWY6zAyUA
5.威胁情报的应用:整合事件响应工作流

事件响应生命周期- 美国国家标准技术研究所
| 定义 | 战术情报 | 作战情报 | 战略情报 |
①.准备阶段 | 在事件响应的准备阶段,包括制定和实施安全防御策略、明确事件响应机制等。 | 引入威胁情报数据并用于SIEM/SOC平台,增加异常告警相关的上下文信息和准确性。 | 明确应对的威胁类型,主要攻击团伙,使用的攻击战术技术特点,常用的恶意代码和工具; 针对上述信息分析内部的攻击面和对应的响应策略。 | 1.全面了解企业面临的威胁类型及其可能造成的影响; 2.了解行业内同类企业面临的威胁类型及已经造成的影响; 3.决策用于应对相关威胁的安全投入。 |
②.检测与分析阶段 | 发现初始异常的告警日志或事件,结合安全检测设备日志、系统日志,进行进一步取证和分析,完成事件定性,来源分析。 | 针对告警提供更丰富的上下文信息,并能聚合其他相关的异常信息,提高安全人员识别的效率。 | 基于威胁情报,明确威胁攻击的类型,来源,针对的目标,攻击的意图。 |
③.隔离、清除与恢复阶段 | 在这个阶段需要对攻击事件做出有效的反应,包括对已失陷设备的隔离、清除恶意攻击活动、对受影响的设备和系统进行恢复,以免遭受的攻击影响面进一步扩大,保障业务和系统正常运转。 | 根据相关的IOC集合针对企业内部资产能够加快评估影响面和损失。 | 基于攻击者的攻击战术技术特点的威胁情报信息,能够帮助安全人员判断当前攻击者已实施的攻击阶段和下一步的攻击行动,针对性进行响应决策。 |
④.事后复盘阶段 | 在事件响应的最后阶段,需要在事后对整个事件响应过程进行复盘和经验总结,并用于完善事件响应和安全防御策略,以避免未来再次遭受同类的攻击。衍生出新的威胁情报共享,为其他相关组织机构提供新的威胁检测能力。 | 发现新的IOC信息作为威胁情报补充到内部威胁情报平台,并用于后续的安全运营工作。 | 帮助完善对整个事件过程的回溯和还原; 更新对攻击者的认知,以更好的应对未来同类的攻击; 结合威胁情报的共享也能够帮助相关行业相关企业应对同类威胁。 |
6.威胁情报的价值呈现
威胁情报的价值主要体现在以下两个方面:
1.提升现有安全产品和服务的防御、检测与响应能力
2.在企业和行业客户的安全架构(漏洞管理)、安全运营(事件监控、事件检测&响应、威胁狩猎)甚至更高层面的风险管理和安全投资上发挥作用。
详细描述如下,
①.充实现有安全技术:通常机读情报以附加订阅方式集成到现有SIEM/IDP等产品中。这一类应用场景的例子还包括TIP(Threat Intelligence Platform) 和TIG(Threat Intelligence Gateway)两类产品。前者实现多源情报管理和分发、更为有效地完成情报与SIEM/EDR以及事件响应的下游集成。后者则是事先预打包海量多源机读情报(支持数百万甚至数十亿的威胁指标),并集成到一个特定设备中进行检测和防御,用于扩充现有网络安全解决方案。
②.钓鱼检测:分为用户发起和社区分享两种情况。前者可以采用TIP和自动化编排技术,在发现可疑邮件后,丰富告警上下文、触发自动化调查流程并根据调查结果联动SIEM。后者主要是新的钓鱼威胁被发现后,通过情报共享机制触发。
③.漏洞优先级管理:Gartner在最新的报告《实施基于风险的漏洞管理方法》中明确,过去十年大约八分之一的漏洞事实上是被在野利用,而这些漏洞在远控木马、勒索软件等广泛威胁中被大量重复利用。CVE编号和CVSS 作为初始的漏洞分类至关重要,但缺乏考虑“攻击团伙实际在做什么”这一要素。基于上述研究,Gartner认为漏洞管理的第一优先级应该是考虑“您的哪些漏洞正被在野利用”。威胁情报集成到漏洞管理中,能为企业提供一种能力,也即确定“哪些漏洞是我数字业务的最大风险”。这是目前应用威胁情报最实用和有价值的使用场景之一。
④.深网以及暗网监控:这类服务的一个价值主张是,分析师代表客户去做。分析师积极渗透深网和暗网这类地下信息交流,需要多年的情报经验。分析师具备的这类技能极为珍稀,往往需要多年的工作积累才能达到从业者的技能水平。对客户的价值则是,客户可以使用这些服务事先获得威胁预警、理解威胁(它们是如何工作的、在哪里被发现),是否有人谈论客户的组织,并且通常是从TTP 角度来了解攻击团伙。
⑤.事件调查和响应:事件响应是威胁情报最重要的应用场景之一。据了解,现在国内有的情报厂商,安服人员使用自己公司的情报平台完成分析报告已经是常规动作。正如杀链模型所描述的,应用情报和安全分析可能在入侵前期就进行响应而不是等到失陷之后才做响应,可以缩短现在业内常说的MTTD时间。
⑥.攻击团伙跟踪:Gartner认为这是最先进的威胁情报用例之一,它往往需要大量的人员配置和技术,并长期投入。一旦建立起这种能力并积累相关的TTP,对于跟踪方,攻击团伙的行为就会浮现而且经常会重复。这是威胁情报能发挥积极主动之处。
⑦.情报分析师调查工具:这是今年报告中新增的一个用例。是指分析师日常依赖的专用工具,为情报分析师、安全运营人员、威胁猎手、事件响应和取证专家所广泛使用。它们支持如下任务:允许安全和匿名访问互联网用于研究;提供有预建工具和其他角色属性(如语言)的托管虚拟桌面;用于事件调查的临时资产,在失陷的情况下不会留下调查人员任何有意义的痕迹;支持基于团队的调查等。
7.威胁情报和ATT&CK™模型
我们前面已经讲过,ATT&CK(对手战术、技术及通用知识库)是一个反映各个攻击生命周期的攻击行为的模型和知识库,而威胁情报是对攻击者及其恶意活动的可运营的知识(actionable knowledge)和洞见(insight),其中知识包括上下文、机制、指标、含义和可执行的建议。因此我们可以利用ATT&CK模型来增强威胁情报。
在继续之前,先尝试回答以下问题?
①.我们的对手是谁?(业余黑客?专业黑客组织?还是超强能力网空威胁行为体?)
②.对手的能力如何?
③.对手最常用的技战术是什么?
④.我们跟对手的差距在哪里?
⑤.我们如何防御?
(一)、利用ATT&CK知识库中已映射的APT组织来改善我们的防御
具体操作步骤如下,
首先,明确自己所在公司的行业性质,前文我们已经讲过威胁情报的四个主要属性之一:相关性,从历史APT组织分析报告来看,APT组织都有明确的目标,APT组织具有地域性、行业性特征,比如FIN4主要针对医疗(healthcare)、制药(pharmaceutical)、金融(financial)行业。
然后,在ATT&CK已映射的APT组织中(https://attack.mitre.org/groups/)查找公司所属行业(这里假设是healthcare /医疗)对应的APT组织,可以通过关键字“healthcare”搜索
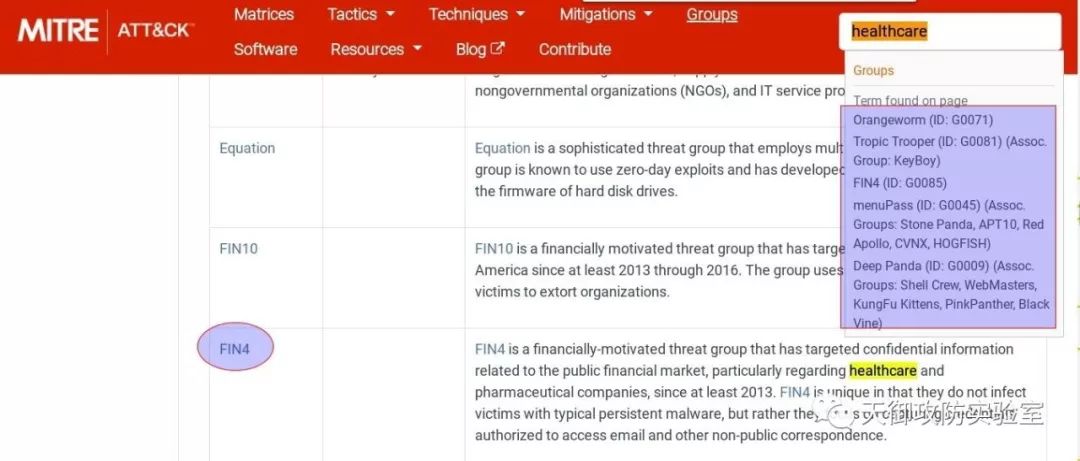
我们发现,FIN4是一个针对医疗、制药、金融行业,有经济动机的黑客组织。2013年以来,FIN4黑客组织已经攻击了超过100家上市公司。该黑客组织专门攻击美国上市企业,窃取它们内部的并购、收购情报。目前FIN4入侵的100多家公司中,有超过2/3属于医疗和制药行业。
第三步,在ATT&CK™ Navigator(https://mitre-attack.github.io/attack-navigator/enterprise/)中分析FIN4使用的TTPs,通过分析可以初步还原FIN4组织的入侵过程,如下
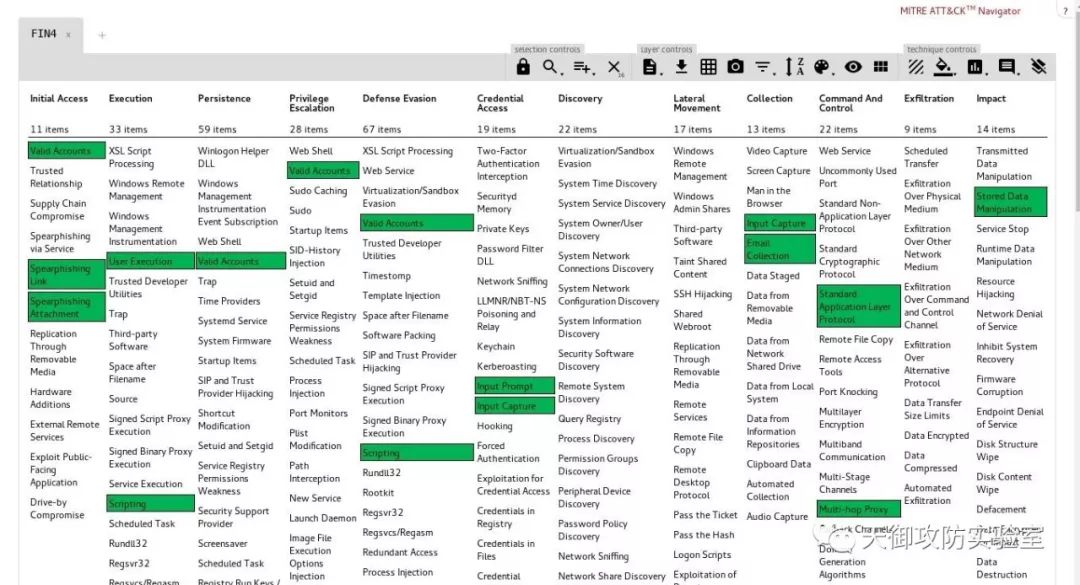
其主要采用盗用邮箱账户入侵的方法。黑客们通过钓鱼邮件当作诱饵来吸引投资者和股东们的关注,而邮件里包含了一个嵌入了VBA宏的Microsoft Office文档,当用户打开这一文档时,它会突然弹出一个Outlook对话框(T1064),让用户填写登录凭证。然后通过HTTP POST请求将盗窃的凭证发送到攻击者控制的服务器。
第四步,通过对FIN4组织的TTPs的具体分析,改善我们的防御
FIN4使用的技术
Domain | ID | Name | Use |
|---|
Enterprise | T1114 | Email Collection | FIN4使用盗窃的凭证访问和劫持电子邮件通信。 |
Enterprise | T1056 | Input Capture | FIN4通过仿冒Outlook Web App(OWA)登录页面捕获凭据,并且还使用了.NET的键盘记录程序(keylogger)。 |
Enterprise | T1141 | Input Prompt | FIN4向受害者提供了欺骗性的Windows身份验证提示,以收集他们的凭据。 |
Enterprise | T1188 | Multi-hop Proxy | FIN4使用Tor登录受害者的电子邮件帐户。 |
Enterprise | T1064 | Scripting | FIN4使用VBA宏来显示对话框并收集受害者凭据。 |
Enterprise | T1193 | Spearphishing Attachment | FIN4使用包含附件(通常是被盗的,从受感染的帐户发送的合法文件)的带有嵌入式恶意宏的鱼叉式钓鱼电子邮件。 |
Enterprise | T1192 | Spearphishing Link | FIN4使用了包含恶意链接的鱼叉式网络钓鱼电子邮件(通常是从受感染的帐户发送的)。 |
Enterprise | T1071 | Standard Application Layer Protocol | FIN4使用HTTP POST请求来传输数据。 |
Enterprise | T1492 | Stored Data Manipulation | FIN4在已受害者的Microsoft Outlook帐户中创建规则,以自动删除包含“黑客”,“网络钓鱼”和“恶意软件”等字词的电子邮件,以防止组织就其活动进行沟通。 |
Enterprise | T1204 | User Execution | FIN4诱骗已受害者点击通过鱼叉式钓鱼电子邮件(通常从受感染的帐户发送)发送的恶意链接和恶意附件。 |
Enterprise | T1078 | Valid Accounts | FIN4使用合法凭据来劫持电子邮件通信。 |
这里我们以规避防御(Defense Evasion)阶段所使用的技术解释脚本/Scripting(T1064)为例进行说明。
在FIN4组织详细描述页面中(https://attack.mitre.org/groups/G0085/)点击T1064,会跳到技术对应的详细描述页面(https://attack.mitre.org/techniques/T1064/)如下,
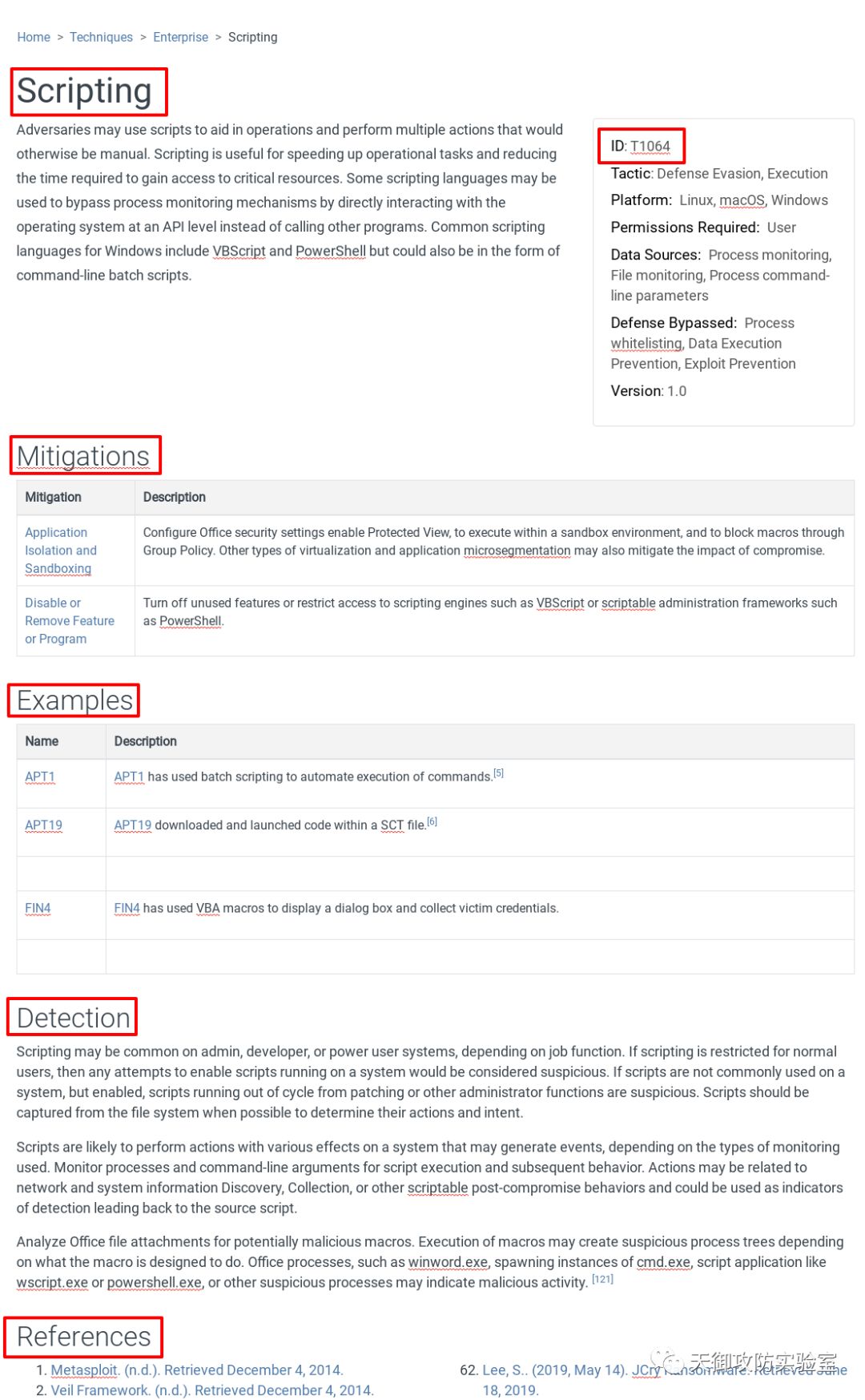
此页面由六个部分组成:
1.技术名称- 技术的详细介绍
2.技术ID – 知识库中技术的唯一标识符。
- Tactic:技术所能达到的战术目标。技术可以用来执行一个或多个战术。
- Platform:对手操作的系统;技术可以应用于多个平台。
- Permissions Required/所需权限:对手在系统上执行该技术所需的最低权限级别。
- Data Sources:传感器或日志系统收集的信息源,可用于收集与识别正在执行的操作、操作顺序或对手操作结果相关的信息。
- Defense Bypassed/绕过防御:可用于绕过或规避特定的防御工具、方法或过程,则仅适用于防御规避技术。
3.Mitigations/缓解措施- 包括配置、工具和过程。
4.Examples/例子- 哪些APT组织使用了此项技术。
5.Detection/检测建议- 用于可识别对手所使用的技术的分析过程、传感器、数据和检测策略。
6.References/参考- 参考资料,其中包括MITRE团队创建此技术的APT报告。
我们重点关注Mitigations和Detection部分,
Mitigations:
- 配置Office安全设置启用受保护的视图
- 在沙箱环境中执行
- 通过组策略阻止宏
Detection:
- 在禁止脚本运行的系统上,尝试启用脚本的动作都可以认为是可疑行为。
- 在允许脚本运行的系统上,非patching或其他管理员功能运行的脚本也可以认为是可疑的。
- 监视脚本执行和后续行为的进程和命令行参数。
- 分析可能存在恶意宏的Office文件附件。执行宏可能会创建可疑的进程树,具体取决于宏的设计目的。Office进程(如winword.exe,生成cmd.exe实例,脚本应用程序(如wscript.exe或powershell.exe)或其他可疑进程)可能表示存在恶意活动。
(二)、利用ATT&CK聚合威胁情报,实现防御升级
前文提到,使用ATT&CK知识库中存在的关于APT组织的相关信息可以帮助企业改善其防御。而这种信息主要来自于安全厂商或安全研究团队公开的APT组织的报告(由MITRE公司将这些信息映射到ATT&CK知识库)。
毫无疑问,这种信息并不能全面反映对手的行为,也不能满足企业的特定的需求,对于对手行为的跟踪必然是一个不断迭代的过程,因此,我们需要利用ATT&CK威胁分析模型对威胁情报进行聚合(将内部和外部信息映射到ATT&CK,包括APT报告、事件响应数据、来自OSINT或威胁情报订阅的报告、实时告警以及组织的历史信息。),使我们能够更深入地了解对手的行为,以帮助确定组织中防御的优先级。
由于各企业的安全建设成熟度及行业相关性的特征,因此我们选择演示如何将公开的APT组织报告映射到ATT&CK,而忽略实时告警、组织的相关信息及事件响应数据等相关信息。
具体操作步骤(以APT3为例)如下,
1.建立自己的ATT&CK知识库管理平台,可以将数据存储在TAXII服务器,STIX 2.0 JSON文件,MISP,前端展示可参考MITRE ATT&CK官网。详细操作步骤请参考:https://github.com/mitre/cti/blob/master/USAGE.md
2.找出APT3的分析报告-参考ATT&CK的Groups(https://attack.mitre.org/groups/G0022)页面的References部分
3.理解ATT&CK的整体结构,熟悉攻击杀伤链、FireEye攻击生命周期
4.找出行为(比如,“建立SOCKS5连接。”)
5.研究行为(SOCKS5是第5层(会话层)协议)
6.将行为转化为战术(上述行为属于战术- “命令与控制”)
7.找出适用于该行为的技术(SOCKS,标准非应用层协议对应技术为:T1095)
8.将您的分析结果与其他分析师比较
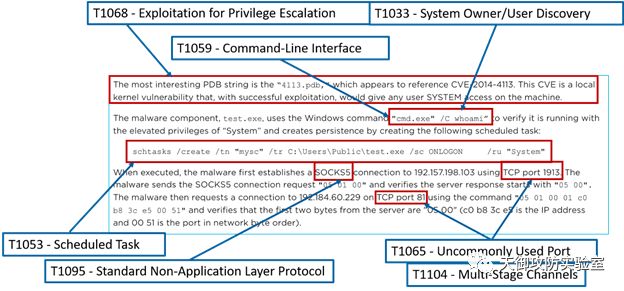
图:APT3映射示例
完成映射后, 我们使用ATT&CK Navigator对专门针对金融机构的APT组织(APT3和APT29)进行对比分析(注意:我们可以将自己映射好的APT3对应的JSON文件导入ATT&CK Navigator),其结果如下,
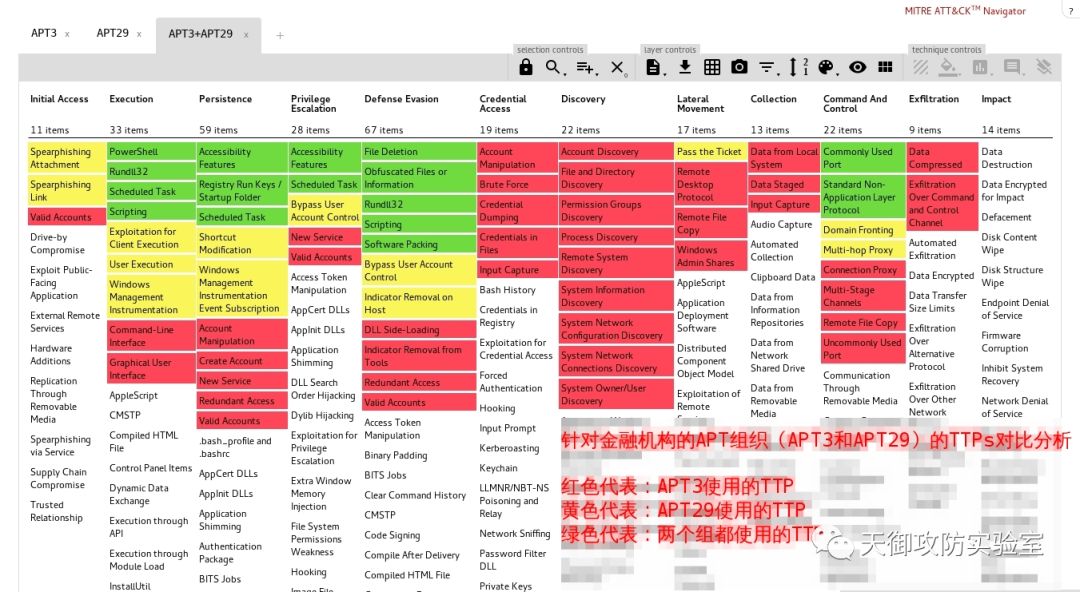
针对金融机构的APT组织(APT3和APT29)TTPs对比分析
通过创建heatmap,可以从以下几个维度帮助我们进行防御升级。
- 最常用技术(图中绿色部分),通过这个信息可以帮助我们调整和优化防御的优先级。
8.参考资料!
ATT&CK™相关技术文档下载地址:
链接:
https://pan.baidu.com/s/1FfuMtRW0Bx87F5VPX7ll4w
提取码:J2ms
--------------------------------------------------------------------------------
官方技术报告
MITRE ATT&CK™: Design and Philosophy
https://www.mitre.org/sites/default/files/publications/pr-18-0944-11-mitre-attack-design-and-philosophy.pdf
Finding Cyber Threats with ATT&CK-Based Analytics
https://www.mitre.org/sites/default/files/publications/16-3713-finding-cyber-threats%20with%20att%26ck-based-analytics.pdf
Dragos_Industrial-Control-Threat-Intelligence-Whitepaper.pdf
https://atr-blog.gigamon.com/2019/07/23/abadbabe-8badf00d-discovering-badhatch-and-a-detailed-look-at-fin8s-tooling
https://www.welivesecurity.com/2019/07/11/buhtrap-zero-day-espionage-campaigns/
"Meet Me in the Middle: Threat Indications & Warning to enable..." - Joe Slowik
https://www.youtube.com/watch?v=vWHAL5fTveM&feature=youtu.be
The_Threat_Intelligence_Handbook.pdf
MISP-CIRCL-ATTACK.pdf
情报驱动应急响应(Book)
威胁情报的三种类型
https://www.jianshu.com/p/854d49c8378b
威胁情报相关标准简介 (上/下篇)
https://www.secrss.com/articles/6599
https://www.secrss.com/articles/6765
汪列军
威胁情报的层次分析
威胁情报的上下文、标示及能够执行的建议
威胁情报在应急响应中的应用
https://ti.360.net/blog/articles/level-of-threat-intelligence/
https://ti.360.net/blog/articles/something-about-threat-intelligence/
https://ti.360.net/blog/articles/application-of-threat-intelligence-in-emergency-response/
威胁情报的价值(Viola_Security)
https://www.jianshu.com/p/7917bb6c1786
事件响应的生命周期
https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf
https://digital-forensics.sans.org/blog/2010/09/27/digital-forensics-security-incident-cycle/
https://blogs.cisco.com/security/dissecting-a-breach-the-process-of-incident-response
Advanced Persistent Threat Groups
https://www.fireeye.com/current-threats/apt-groups.html
对提升入侵检测能力的一点思考(Mils)
https://mp.weixin.qq.com/s/0SDHshDvARx4gBPyLzkR3A
浅谈大型互联网的企业入侵检测及防护策略(职业欠钱)
https://mp.weixin.qq.com/s/1Iry620hCkJ8sHA626T3Dg
从ATT&CK看威胁情报的发展和应用趋势 (小强)
https://mp.weixin.qq.com/s/zbAwTDZ5IuRCMkuIDo82Cw
9.致谢!
此次写作的初衷:集业界众安全专家的智慧,系统、全面地介绍以下主题,
- ATT&CK™
- 威胁情报
- 威胁检测和威胁猎杀
- 红蓝军对抗模拟
笔者在写作的过程中,深感要实现这个目标十分艰巨!因此,把目前所学、所思记录下来,后续再完善。
此次写作参考了以下安全团队及个人的研究成果,(排名不分先后)
安天(Cert)
Freddy Dezeure
Katie Nickels@MITRE
Joe Slowik
Mils
Sergio Caltagirone@Dragos
肖岩军@NSFOCUS
小强
余凯总@瀚思科技
Viola_Security
职业欠钱总@美团安全
ZenMind
汪列军@奇安信威胁情报中心/360威胁情报中心
(Corelight Labs、Reservoir Labs、Red Canary、Endgame、FOX IT、SpecterOps Team、Sqrrl、FireEye、
Awake Security、Gigamon Applied Threat Research Team、SANS Institute、Cisco Talos、Proofpoint等)
特别说明:此专栏绝非笔者一人之力所能成,没有各位同行的无私分享,此专栏也不可能出现!
特别感谢:有幸能向周奕总@瀚思科技、袁明坤总@安恒信息、杨大路总@天际友盟请教,受益匪浅!
每个人的知识、能力和视野终归有限,恳请安全行业的前辈、兄弟姐妹批评指正!