INTRODUCTION
Following our successful article Understanding Cisco Dynamic Multipoint VPN - DMVPN, mGRE, NHRP, which serves as a brief introduction to the DMVPN concept and technologies used to achieve the flexibility DMVPNs provide, we thought it would be a great idea to expand a bit on the topic and show the most common DMVPN deployment models available today. This will provide an insight to engineers and IT Managers considering implementing a DMVPN network.
Those seeking help to configure a DMVPN network can also refer to our Configuring Cisco Dynamic Multipoint VPN (DMVPN) - Hub, Spokes , mGRE Protection and Routing - DMVPN Configuration article which fully covers the deployment and configuration of a Single DMVPN Network/Cloud - Single Tier Headend Architecture.
DMVPN DEPLOYMENT MODELS
There is a number of different ways an engineer can implement a DMVPN network. The fact that there is a variety of DMVPN models, each one with its caveats and requirements, means that almost any VPN requirement can be met as long as we have the correct hardware, software license and knowledge to implement it.
Speaking of implementation, no matter how complex the DMVPN network might get, it’s pretty straightforward once it's broken down into sections.
Engineers already working with complex DMVPNs can appreciate this and see the simplicity in configuration they offer. At the end, it’s all a matter of experience.
Providing configuration for each deployment model is out of this article’s scope, however, we will identify key services used in each deployment model along with their strong and weak points.
Future articles will cover configuration of all DMVPN deployment models presented here.
Following are the most popular DMVPN deployment models found in over 85% of DMVPN networks across the globe:
- Single DMVPN Network/Cloud - Single Tier Headend Architecture
- Single DMVPN Network/Cloud - Dual Tier Headend Architecture
- Dual DMVPN Network/Cloud – Single Tier Headend Architecture
- Dual DMVPN Network/Cloud – Dual Tier Headend Architecture
In every case a complete DMVPN deployment consists of the following services, also known as control planes:
- Dynamic Routing (Next Hop Resolution Protocol)
- mGRE Tunnels
- Tunnel Protection – IPSec Encryption that protects the GRE tunnel and data
It’s time now to take a look at each deployment model.
SINGLE DMVPN NETWORK/CLOUD - SINGLE TIER HEADEND ARCHITECTURE
This deployment model is DMVPN in its simplest form. It consists of the main Hub located at the headquarters and remote spokes spread amongst the remote offices.
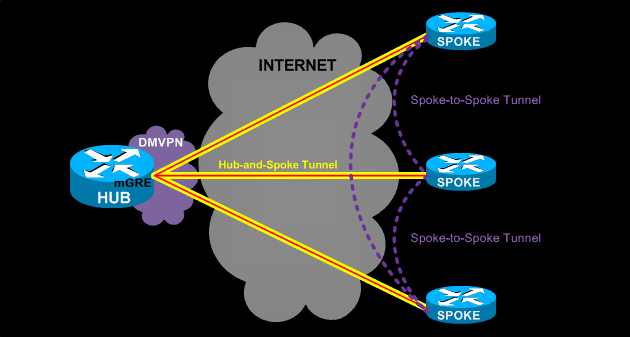
The term ‘Single DMVPN’ refers to the fact there is only one DMVPN network in this deployment. This DMVPN network consists of the yellow GRE/IPSec Hub-and-Spoke tunnels terminating at the central Hub from one end and the remote spokes on the other end.
The term ‘Single Tier Headend’ means that all control planes are incorporated into a single router – the Hub. This means it takes care of the dynamic routing (NHRP), mGRE tunnels and IPSec Tunnel Protection.
The central hub maintains the Next Hop Resolution Protocol (NHRP) database and is aware of each spoke’s public IP address.
When setting up a DMVPN network, every spoke is configured, using static NHRP mappings, to register with the Hub. Through this process, every spoke is aware of every other’s public IP address via the NHRP server (Hub), no matter if the spokes IP addresses are dynamic or static.
Through DMVPN, each spoke is able to dynamically build a VPN tunnel to each other spoke, allowing the direct communication between them without needing to tunnel all traffic through the main Hub. This saves valuable bandwidth, time and money.
We should at this point note that in Phase 1 DMVPN, all traffic passes through the Hub. Phase 2 and Phase 3 DMVPN, directly forms spoke-to-spoke tunnels and sends traffic directly, bypassing the Hub.
The Single DMVPN - Single Tier Headend Architecture has the advantage of requiring only one Hub router, however, the Hub’s CPU is also the limiting factor for this deployment’s scalability as it undertakes all three control planes (NHRP, mGRE & IPSec protection).
In addition the Hub router, and its link to the Internet, is the single point of failure in this design. If any of the two (Hub or Internet link) fail, it can cripple the whole VPN network.
This DMVPN model is a usual approach for a limited budget DMVPN network with a few remote branches. Routing protocols are also not required when implementing a single DMVPN network/cloud. Instead, static routes can be used with the same end result.
SINGLE DMVPN NETWORK/CLOUD - DUAL TIER HEADEND ARCHITECTURE
This DMVPN deployment consists of two routers at the headquarters. The first router, R1, is responsible for terminating the IPSec connections to all spokes, offloading the encryption and decryption process from the main Hub behind it. The Hub router undertakes the termination of mGRE tunnel, NHRP server and processing of all routing protocol updates.
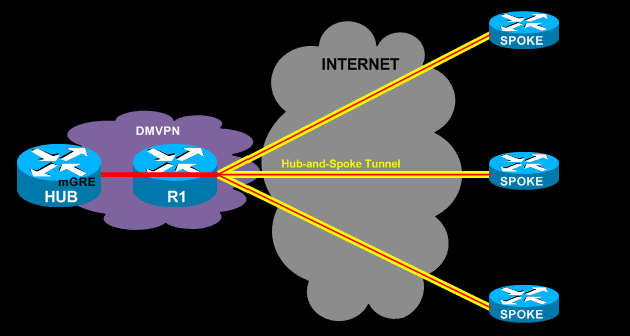
The only real advantage offered by the Dual Tier Headend Architecture (Single DMVPN cloud) is that it can support a significantly greater number of spokes.
A limitation of Dual Tier Headend Architecture is the absence of the spoke-to-spoke connections, in Dual Tier DMVPN spoke-to-spoke connections are not supported.
DUAL DMVPN NETWORK/CLOUD – SINGLE TIER HEADEND ARCHITECTURE
The Dual DMVPN topology with spoke-to-spoke deployment consists of two headend routers, Hub 1 and Hub 2. Each DMVPN network (DMVPN 1 & DMVPN 2) represents a unique IP subnet, one is considered the primary DMVPN while the other is the secondary/backup DMVPN.
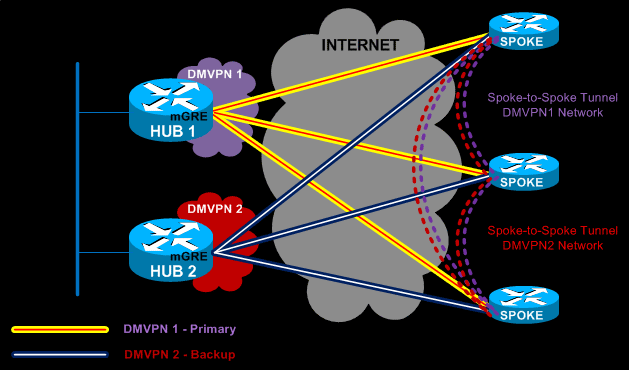
The dynamic Spoke-to-Spoke tunnels created between branches must be within a single DMVPN network. This means that spoke-to-spoke tunnels can only be created between spokes in the same DMVPN network.
With Dual DMVPN – Single Tier Headend Architecture, each Hub manages its own DMVPN network. Each Hub undertakes the task of IPSec encryption/decryption, mGRE Tunnel termination and NHRP Server for its DMVPN network. A routing protocol such as EIGRP or OSPF is usually implemented in this type of setup to ensure automatic failover in case the primary DMVPN fails.
Dual DMVPN – Single Tier Architecture is considered an extremely flexible and scalable setup as it combines the best of both worlds – that is, true redundancy with two separate Hubs and DMVPN networks, plus support for spoke-to-spoke tunnels.
DUAL DMVPN NETWORK/CLOUD – DUAL TIER HEADEND ARCHITECTURE
The Dual DMVPN Network – Dual Tier Headend combines the previous two deployment methods in one setup.
The Dual DMVPN Network – Dual Tier Headend consists of two Hubs that deal only with mGRE tunnels and NHRP services, each Hub managing its own DMVPN network.
Frontend routers R1 and R2 take care of all IPSec termination for all spokes, performing encryption/decryption as data enters or exits the IPSec tunnels.
Newer ISR G2 routers are capable of undertaking great quantities of number crunching for all VPN tunnels as they are equipped with hardware accelerated VPN modules that offload this process from the main CPU.
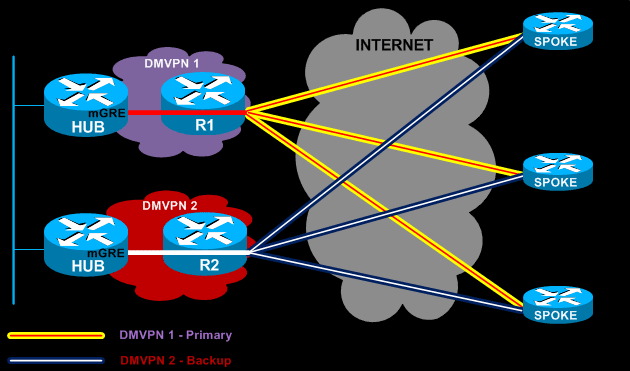
As with Dual DMVPN – Single Tier deployment model, each Hub manages its own DMVPN network and connections with its spokes. Routing protocols are a necessity to ensure automatic failover to the secondary DMVPN network in case the primary fails.
Unfortunately, as with all Dual Tier deployments, we lose the spoke-to-spoke ability, but this might not be a limitation for some.

No comments:
Post a Comment